
Attackers don’t need AGI
The largest international AI safety review has landed – and for cybersecurity teams, the message is that attackers don’t need AGI to cause serious damage
Read More
Welcome to the new 126 cyber warriors who joined us last week. Each week, we'll be sharing insights from the Black Hat MEA community. Read exclusive interviews with industry experts and key findings from the #BHMEA stages.
Keep up with our weekly newsletters on LinkedIn — subscribe here.
Our weekly delivery of cybersecurity insights and exclusive interviews – here in your inbox.
The physical threat landscape.
The threat landscape extends beyond the cyber world, and into our physical environment – because threat actors are willing to exploit any vulnerability. Even if it involves brute force.
As the digital threat landscape becomes bigger and more complex, it’s easy to focus on technological entry points to networks and data. But as an industry, we have to remember that the ‘cyber’ in cybersecurity doesn’t mean it’s not physical – and for some victims, an attack starts with a very real, physical crime.
Today, cyber criminals are experimenting with new ways to reach targets. And those methods absolutely do include IRL exploitation.
In an interview with Delano, Pierre Zimmer (Deputy Managing Director of POST Luxembourg) said:
“We are indeed seeing bold developments in the modus operandi of attackers. Increasingly, criminals are seeking to act in the real world, where the level of distrust is lower than in the digital world.”
It’s an ironic development, really: that pushing for cyber awareness and rolling out comprehensive cybersecurity training programs across industries is increasing barriers-to-entry for threat actors, and pushing them to operate face-to-face, where they’re more likely to be trusted (or at least, trusted for long enough to get what they need).
For example, an invoice received in the post is more likely to be assumed genuine, and therefore paid quickly – before the recipient considers whether it might have been posted nefariously.
Today, companies are increasingly automating elements of their operations management with remote endpoints – such as IoT devices to monitor the production or distribution of energy, for example; or unattended payments services in retail stores and private buildings.
Some of these remote installations are beginning to process sensitive customer data, as AI enhances their functional capabilities.
This creates a new attack surface for threat actors: remote systems that are connected to an organisation’s network, and that might house sensitive data in their own right.
It’s essential that organisations take all of these installations into account when undertaking penetration testing – because a growing network of endpoints creates the potential for unguarded vulnerabilities.
Simultaneously, critical remote installations should be diversified in order to make sure the organisation isn’t dependent on one technology – so if that technology is compromised or exposed, its role in the network can be contained, and the organisation’s wider operations can continue.

According to a recent Elastic report on global threats, there has been a 12% increase in brute force cyberattack techniques in 2024.
And in the EU, an investigation by cybersecurity firm Heimdal found that corporate and institutional networks are facing a surge in brute force attacks.
Key findings from Heimdal include:
This means that cybersecurity operations must include comprehensive and continuous monitoring of networks, including all endpoints – and a drive to educate individuals and organisations about the risks of physical and brute force attacks.
Have you observed a rise in cyberattacks that leverage vulnerabilities in the physical world? Open this newsletter on LinkedIn and share your perspective in the comment section. We might reach out to include your comments in a future newsletter.
Do you have an idea for a topic you'd like us to cover? We're eager to hear it! Drop us a message and share your thoughts. Our next newsletter is scheduled for 30 October 2024.
Catch you next week,
Steve Durning
Exhibition Director
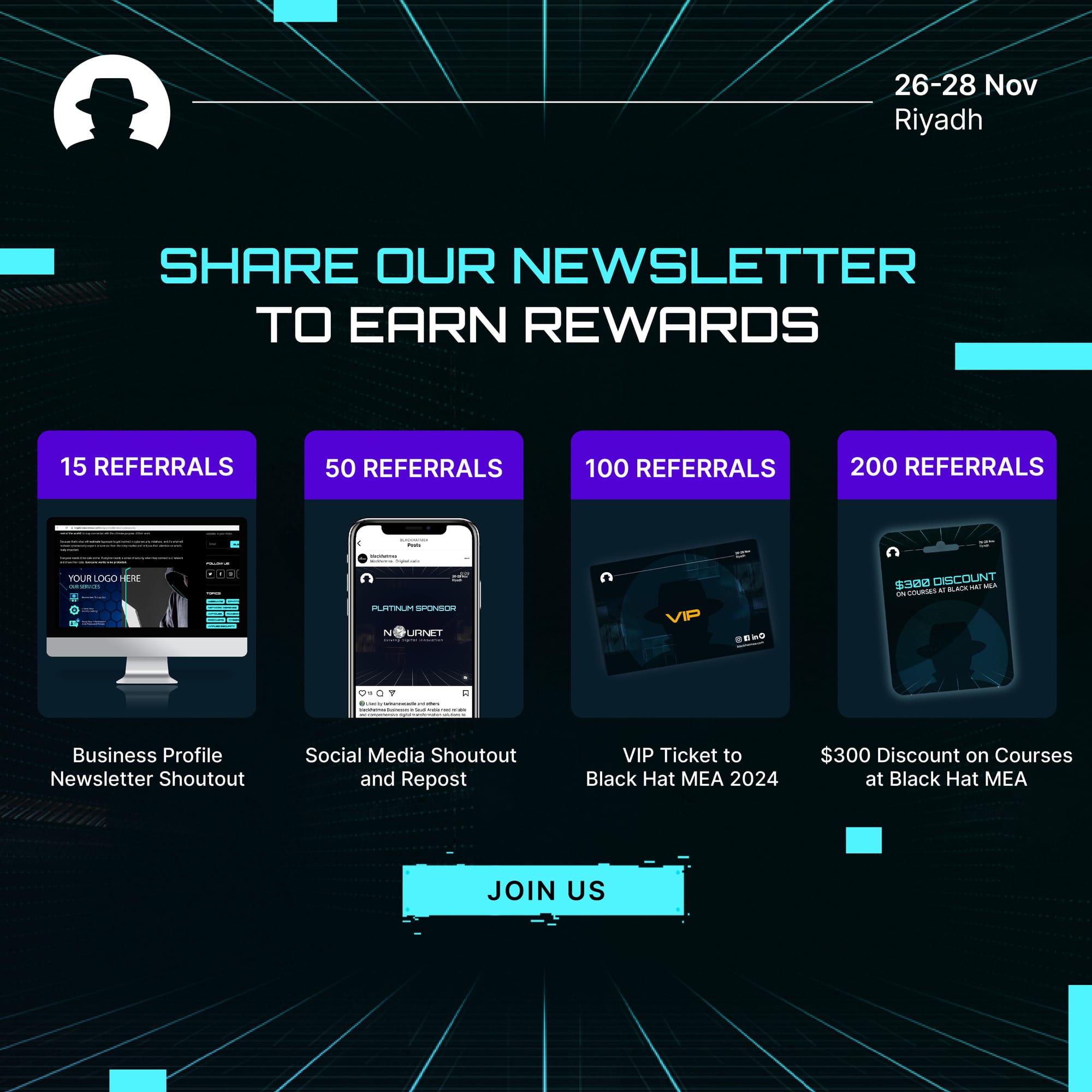
Join us at Black Hat MEA 2024 to grow your network, expand your knowledge, and build your business.
Join the newsletter to receive the latest updates in your inbox.

The largest international AI safety review has landed – and for cybersecurity teams, the message is that attackers don’t need AGI to cause serious damage
Read More
Four exhibitors explain why Black Hat MEA is the region’s most important meeting point for cybersecurity buyers, partners, and talent.
Read More
Why Riyadh has become essential for cybersecurity practitioners – from government-backed momentum and diversity to global collaboration and rapid innovation at Black Hat MEA.
Read More