
When privacy creates blind spots: the exploitation of privacy-first tech
New research reveals how privacy-first technologies are creating fraud blind spots, as AI-driven attacks scale faster than detection capabilities.
Read More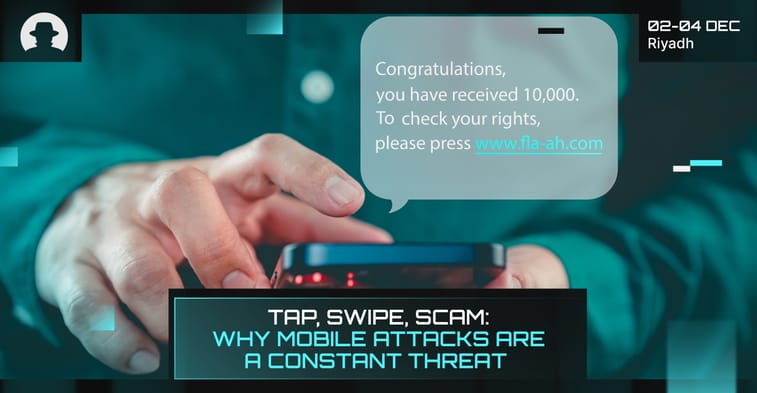
Even security-savvy mobile users are getting caught out – tapping malicious links, scanning fake QR codes, and responding to messages that seem just believable enough.
According to Malwarebytes’ Tap, Swipe, Scam report in March 2025, nearly half of mobile users encounter scams daily – and a staggering 75% have faced social engineering attempts like phishing or impersonation scams.
What’s driving this rise in mobile fraud, and why are hackers increasingly focused on our phones?
Mobile phones are always on. We shop, chat, bank, and work from them. As the Malwarebytes report puts it, mobile phones are now the ‘new frontline of digital deception’; and for hackers, that’s gold.
The report outlines three key reasons for this shift towards mobile threat:
These habits leave us exposed; and hackers know it.
The rising danger of mobile scams is closely linked to how convincing they’ve become. According to Malwarebytes’ research, two-thirds of people say it’s hard to tell a scam from the real thing, and only 15% feel confident spotting one. On top of that, people know the situation is likely to get worse – 66% are worried about how realistic scams are going to get in the future thanks to AI.
We're seeing a surge in deepfake extortion scams, impersonation attempts, and smishing attacks that feel like they’re from your bank, your friend, or your delivery service.
Back at Black Hat MEA 2022, mobile security expert Georgia Weidman (Founder and CTO at Shevirah and Bulb Security LLC) spoke about why mobile devices are such a big risk:
“As soon as we started allowing mobility into our network, all of those assumptions broke down. We no longer had control over even understanding what all the devices were on our network.”
Weidman pointed out that mobile devices can be used to pivot inside a network – letting attackers bypass traditional defences to access other systems. And because many organisations still don’t include mobility in their pen testing, those risks are often invisible until it’s too late.
Attacks against mobile devices don’t just hit the victim’s wallet. They impact your mental health, your trust in others, and even your sense of safety. Malwarebytes found that 75% of scam victims experienced emotional consequences, and nearly half struggled with anxiety, stress, or depression.
And while Gen Z are the most digitally savvy generation, they’re also the most targeted. More than a quarter have fallen victim to high-impact scams like deepfakes or virtual kidnapping – threats that leave lasting emotional scars.
Despite all this, fewer than one in five users report scams or use security tools. In fact, one in four say they’ve simply stopped caring – accepting scams as the price of being online.
That’s a dangerous mindset. Because while we’re giving up, hackers are just getting started.
As Weidman warned:
“Unfortunately what we don’t really have is a lot of oversight into what our vulnerabilities are.”
We need that oversight. Both on an organisational level and a personal level; we need to understand where and why we’re vulnerable. Awareness matters because it drives action – basic security tools, managing app permissions, and being cautious about clicks are simple ways to reduce risk.
For organisations, education is essential right now. Tell your employees they shouldn’t accept scams as inevitable. Start protecting mobile devices as critical network endpoints; and absolutely include mobile tech in pen testing and security development.
Join the newsletter to receive the latest updates in your inbox.

New research reveals how privacy-first technologies are creating fraud blind spots, as AI-driven attacks scale faster than detection capabilities.
Read More
Cybersecurity founders share how Black Hat MEA helps them test ideas, prove product value, and grow their business.
Read More
Cybersecurity is now a leading barrier to financial innovation. New research explains why fraud, legacy systems and risk are slowing payments progress.
Read More