
Securing the Internet of Things: Thousands of IP cameras hacked
The latest in a long line of attacks against IoT devices that highlights the vulnerability of the Internet of Things.
Read More
YOUR GUIDE TO THREAT HUNTING WITH OPEN-SOURCE TOOLS
The growing risk of cyber-attacks in today’s increasingly dynamic environment calls for robust threat hunting techniques. According to the 2022 Threat Hunting Report by Cybersecurity Insiders, 56% of organisations reported an increase in threat levels during the past year. The main purpose of threat hunting is to detect and identify threats quickly and make you respond faster. This cuts the dwell time of adversaries in the environment and makes your approach to cybersecurity more proactive. Cybercriminals get stealthier by the day, and once they breach a network, they can easily hide their activities from traditional threat detection tools like sandboxes, antimalware, and antivirus solutions. Thus, threat hunting can help you pinpoint suspicious behaviour that could herald a breach and identify hidden threats that are already embedded in your enterprise’s networks, devices, and datasets; in fact, 37% of security threats in SOCs are missed, according to the Threat Hunting Report. Security professionals are increasingly recognising the importance of threat hunting in an overall cybersecurity strategy, with 88% of organisations survey agreeing that it should be a top security initiative. So if you’re looking for reliable threat hunting tools without breaking the bank, consider tried-and-true open-source tools that will give you the flexibility to customise them according to your organisation’s needs.
THREAT HUNTING TOOLS WE RECOMMEND
Many smaller businesses decide to rely on open-source threat hunting tools to reduce their cybersecurity costs. These tools are typically freely available online, although choosing the right one could sometimes be challenging. Ultimately, open-source threat hunting platforms are more accessible to people who find professional threat hunting tools too costly. There is a growing recognition that open-source threat hunting, which is freely available and easy to modify, gives you the benefits of cybersecurity without the headache of admin.
On that note, here are some of the open-source threat hunting tools we’d recommend:
CUCKOO SANDBOX
Cuckoo Sandbox is an analytics-driven tool and a pioneer in open-source automated malware analysis systems. It allows you to get rid of any suspicious files and get immediate, detailed results describing what the suspected file did when tested in an isolated environment.
Cuckoo doesn’t simply dispose of the malware it detects; it provides analytics about how the malicious files are functioning to let you comprehend the intended effect of a breach.
YARA
YARA is a multi-platform tool that enables you to categorise malware and create descriptions of related malware categories built upon binary or textual patterns. Every description consists of boolean expressions along with a set of strings and expressions that create its identity.
YARA uses Python scripts or its own command-line interface and runs on Windows, Mac, and Linux. It is often used to improve the performance of commercial software. YARA is officially recommended by CISA to match malware families. It allows you to match byte sequences, strings, and logic operators using precise conditions, which limits false positives.
AIENGINE
You can count on AIEngine to revolutionise your network’s intrusion detection system. This interactive threat hunting tool can learn without human intervention. Plus, it’s programmable and contains features like:
● Network forensics
● Network collection
● Spam detection
APT-HUNTER
APT-Hunter is a free alternative to SIEM solutions which usually require a paid license. The open-source tool was released in 2021, and it analyses the Windows Event Log to discover threats and shady activities. APT-Hunter is rich in over 200 detection rules to help threat hunters manually detect suspicious activities such as pass-the-hash and password spraying attacks.
APT-Hunter gathers Windows logs in both CSV and EVTX formats, producing two output files after execution:
1. .xlsx file containing every event detected as suspicious or malicious
2. .CSV file that Timesketch can load to show the chronological progress of an attack.
DeepBlueCLI
DeepBlueCLI is an open-source threat hunting tool that is available in the SANS Blue Team GitHub repository and can analyse EVTX files from the Windows Event Log. DeepBlueCLI parses logged Command shell and Powershell command lines to detect suspicious indications like regex searches, long command lines, obfuscation, and unsigned EXEs and DLLs. It can also detect attacks on user accounts, such as password guessing and spraying.
SNORT
Snort is an open-source Intrusion Prevention System (IPS) that generates notifications for users on any unusual or malicious activities it identifies. Snort is extremely effective for network traffic debugging and comprehensive threat prevention. You can download and set up the tool for either personal or business use.
Suricata
Suricata is an open-source tool that is owned and supported by the Open Information Security Foundation (OISF), a non-profit which is dedicated to maintaining Suricata’s open-source status forever. It’s a powerful threat hunting tool because it can log HTTP requests, log and store TLS certificates, extract files from flows and store them on disk, all while using a pcap capture support that enables easy analysis.
ZEEK
Zeek is a threat hunting monitoring tool that analyses what it sees to produce compact, high-fidelity transaction logs, file content and fully customised output that can be manually reviewed on disk or in a more analyst-friendly tool like a security and information event management (SIEM) system.
THREAT HUNTING IN THE CLOUD WITH SNORT: A USE CASE
A case study conducted by the Eastern Institute of Technology showed the impact of installing the open-source Intrusion Detection System (IDS) Snort in a cloud environment due to the tool’s high scalability. Snort was deployed on an Ubuntu Server 16.0.4 LTS, a virtual machine (VM) in Microsoft Azure. The study used an architecture based on VM-integrated IDS on Azure and showcased how a virtual machine could be secured on the cloud using IDS. While firewalls are often the primary method of defence, they don’t successfully protect systems from insider attacks. This is where an IDS like Snort comes in. The study showcased how a cloud network can be secured using a distributed placement of the IDS by highlighting a specific IDS architecture for the cloud paired with Snort.
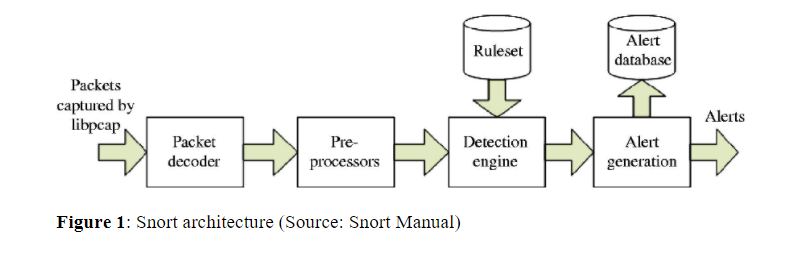
SNORT ARCHITECTURE
Snort is made up of five main components that work together to analyse and monitor all network traffic to detect any signs of intrusion and create alerts.
The five main components are seen in the figure below:
IDS ARCHITECTURE FOR THE CLOUD
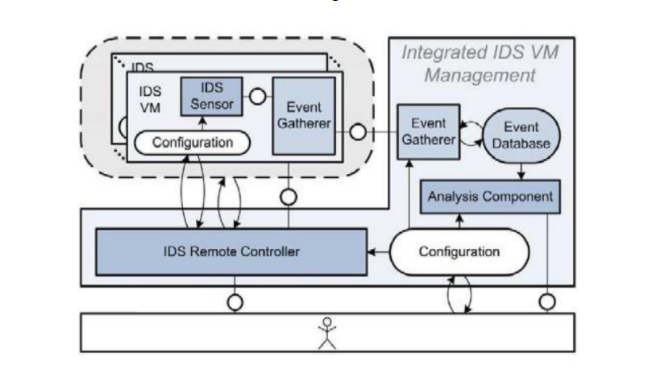
Sebastian Roschke & Christoph Meinel recommended a virtual machine that integrated IDS architecture. It is made up of two main parts, an IDS management unit and an IDS sensor. A built-in event gatherer in the IDS management unit collects unusual behaviour picked up by the IDS sensor and then stores it into an event database. Following that, an analysis component examines these logged events based on the configuration of the database. The IDS Remote Controller communicates with the IDS-VMs and ID sensors and can therefore manage the IDS-VMs. This method of IDS deployment helps secure virtual machines on the cloud and the services running on them.
KEY FINDINGS
The study found that Snort can act as a host-based intrusion detection system when installed on cloud-based virtual machines or as a network intrusion detection system when installed on network interface cards or routers. The main benefit of Snort is that it can be configured to fit the needs of any organisation, and advanced users can create their own rule sets to implement soft computing techniques. Snort is very scalable, costs little to compute, and produces few false positives and negatives. Upon implementation, Snort was able to detect traffic passing through the network interface of the Azure virtual machine. It could also identify a variety of data packet types on the network, such as TCP and TELNET, generating customised alerts based on the defined local rules. A wide range of organisations and businesses can use Snort. However, while installing Snort on a cloud-based virtual machine protects it from malicious activity, it cannot detect intrusions coming from outside of the network. The best course of action would be to place an IDS on a central service to detect both internal and external intrusions. In that procedure, Snort can be paired with another relational database like MySQL or Oracle to log alerts for analysis by a plugin such as Barnyard2. Ultimately, Snort regularly updates the rule sets for new threat signatures, which keeps you ahead of threats.
THREAT HUNTING SHOULD BE A PART OF YOUR OVERALL SECURITY
Threat hunting is a conscious effort by IT security professionals against attackers, and having multiple tools in your arsenal increases your odds of success. So make sure that your business is armed with the solutions that work for it. IT experts stress that threat hunting improves overall security. “Since you are hunting for adversarial activity, the process of threat hunting will give you the chance to examine your IT environment from the perspective of a threat actor. You may not always find a threat over the course of your hunts, but you will almost assuredly find misconfigurations, network anomalies and potential weaknesses by virtue of the exercise. The knowledge gleaned through threat hunting holds value because you can use it to strengthen your overall cybersecurity defenses,” said Tim Crothers, an author and trainer with a long history in cybersecurity.
BOOST YOUR THREAT HUNTING SKILLS AT BLACK HAT MEA
Want to get ahead of threat actors and gain access to a pool of open-source tools? Then join us at Black Hat MEA, where you’ll be accompanied by 200+ global Infosec influencers, including 50 Black Hat trainers and hundreds of ethical hackers, to learn all about threat hunting and pentesing. The renowned Black Hat cybersecurity conference just launched in the Middle East, and it’s not to be missed. Learn from and network with leading CISOs from front-page companies, and sharpen your skills to take your organisation’s security to the next level. Black Hat MEA supports the Saudi Vision 2030 by training people to protect the Kingdom’s ambitious projects from potential threats.
Join the newsletter to receive the latest updates in your inbox.

The latest in a long line of attacks against IoT devices that highlights the vulnerability of the Internet of Things.
Read More
Why cybersecurity offers a long-term career opportunity with strong progression and stability.
Read More
Learn from Irene Corpuz (Founding Partner and Board Member, WiCSME) and understand the challenges ahead for gender diversity in cyber.
Read More