
Attackers don’t need AGI
The largest international AI safety review has landed – and for cybersecurity teams, the message is that attackers don’t need AGI to cause serious damage
Read More
Welcome to the new 202 cyber warriors who joined us last week. Each week, we'll be sharing insights from the Black Hat MEA community. Read exclusive interviews with industry experts and key findings from the #BHMEA stages.
Keep up with our weekly newsletters on LinkedIn — subscribe here.
Healthcare attacks in 2024.
The healthcare sector has become a prime target for cybercriminals, primarily because of the large volumes of sensitive data it handles and stores. Sensitive, personal data is a valuable commodity for threat actors – and patient medical records are as sensitive as it gets.
A breach can expose identity data and detailed health information; and attackers know they can demand a high ransom for this, or cause severe disruption and losses for both organisations and individuals. Importantly, health data has long-term value – people can’t just change it when it’s been stolen, like a credit card number. So obtaining patient data has the potential for rewards in the future, not just the immediate moment.
Beyond the data, the critical, often life-and-death nature of healthcare services means that organisations in this sector are more likely than others to pay ransoms. They simply can’t afford to risk extended service downtime – so they have to be responsive to attackers’ demands.
The American Healthcare Association has recorded 386 healthcare cyberattacks this year at time of writing.
Cybercriminals are serious about disrupting healthcare. So let’s look back at the most serious health sector attacks in 2024 (so far).
In 2024, US healthcare payment provider Change Healthcare disclosed a cyber attack that caused disruption across the nation’s healthcare systems for several weeks.
A ransomware attack triggered the initiation of an IT system shutdown, which prevented a large number of pharmacies, hospitals, and other healthcare facilities from processing claims or receiving payments.
The attack was claimed by BlackCat/ALPHV, and Andrew Witty (UnitedHealth Group CEO) confirmed in May that Change Healthcare paid a ransom of USD $22 million.
Following that payment, a second criminal group, RansomHub, released data it claimed had been stolen from Change Healthcare. The company then reported that the data of a large number of American citizens may have been stolen in the original attack.
In May 2024, non-profit health system Ascension that operates 140 hospitals across 19 US states was targeted in a ransomware attack that disrupted clinical operations.
An employee unknowingly downloaded malware onto the organisation’s network, forcing Ascension to divert emergency care from some of its hospitals, which put patients at risk.
Investigations into the attack found that sensitive data was stolen during the attack, including patient health records. It was a breach that exploited human error, and it highlighted how important it is for organisations to foster a culture of security – driving cyber awareness through training and skills development, and ensuring that all individuals within an organisation understand the role they play, and remain vigilant at all times.
In April 2024, US prepaid health plan and insurance firm Kaiser Permanente notified the national government that a data breach had occurred, affecting 13.4 million people.
Personal health information was shared with third-party entities through a tracking code, which was embedded within pages on the company’s website and mobile app.
The exposed data included names, IP addresses, sign-in and activity data on the Kaiser website and app, and health encyclopaedia search terms. Kaiser removed the tracking code – but not before a large number of users had their data compromised.

Globally, the healthcare industry is at risk. It’s estimated that the sector will spend USD $125 billion on cybersecurity between 2020 and 2025, and one report predicts that global annual healthcare spending will grow from $8 trillion in 2013 to over $18 trillion in 2040.
Equipping healthcare with sufficient cybersecurity systems has been, and continues to be, an immense challenge – hindered by outdated IT systems, low numbers of IT staff, and urgent services that cannot pause operation in order to address breaches or ransom demands.
How can key players in the field of cybersecurity work with healthcare organisations to develop relevant, robust, and viable security operations to protect data and patient safety? Open this newsletter on LinkedIn and share your perspective in the comment section.
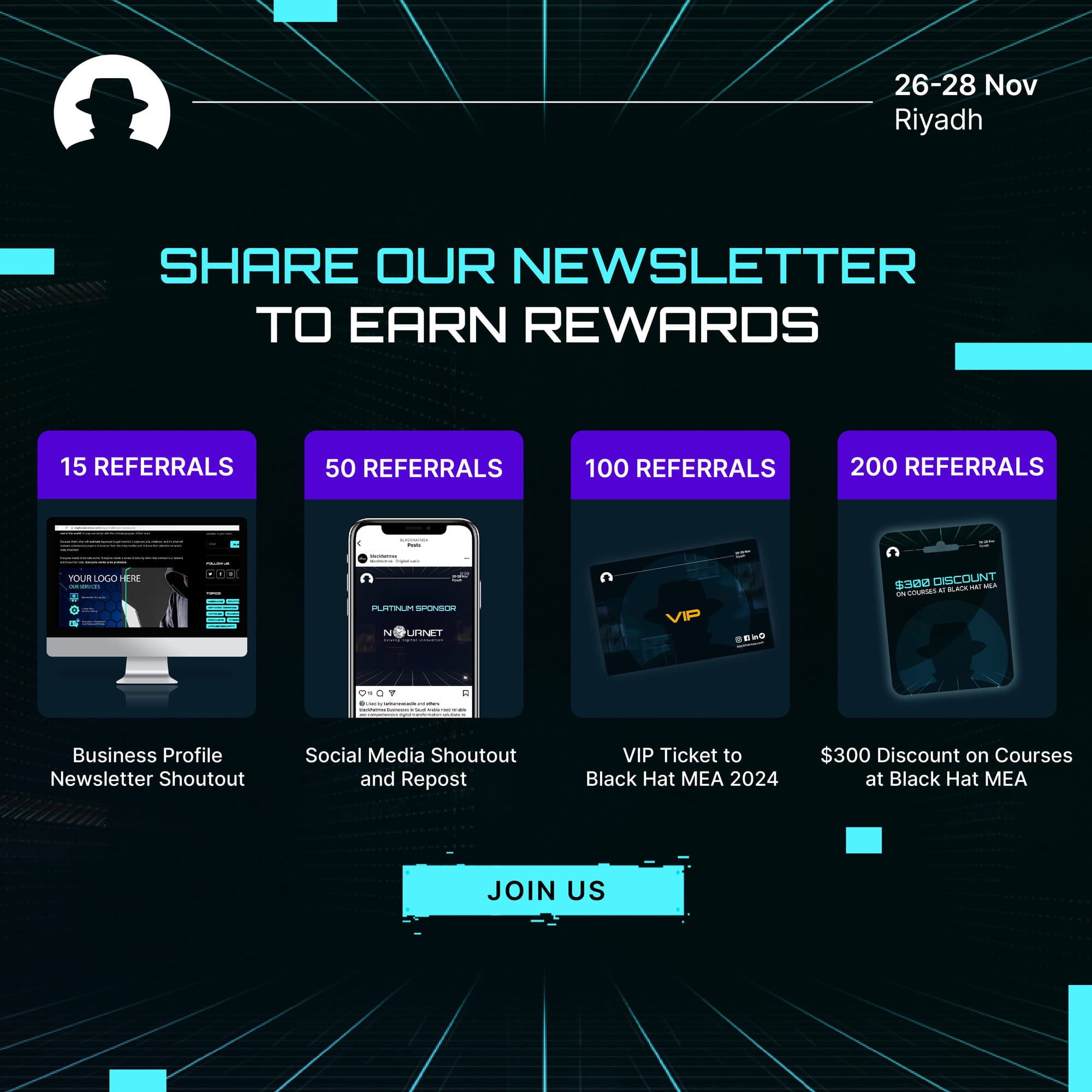
Do you have an idea for a topic you'd like us to cover? We're eager to hear it! Drop us a message and share your thoughts. Our next newsletter is scheduled for 27 November 2024.
Catch you next week,
Steve Durning
Exhibition Director
Join us at Black Hat MEA 2024 to grow your network, expand your knowledge, and build your business.
Join the newsletter to receive the latest updates in your inbox.

The largest international AI safety review has landed – and for cybersecurity teams, the message is that attackers don’t need AGI to cause serious damage
Read More
Four exhibitors explain why Black Hat MEA is the region’s most important meeting point for cybersecurity buyers, partners, and talent.
Read More
Why Riyadh has become essential for cybersecurity practitioners – from government-backed momentum and diversity to global collaboration and rapid innovation at Black Hat MEA.
Read More